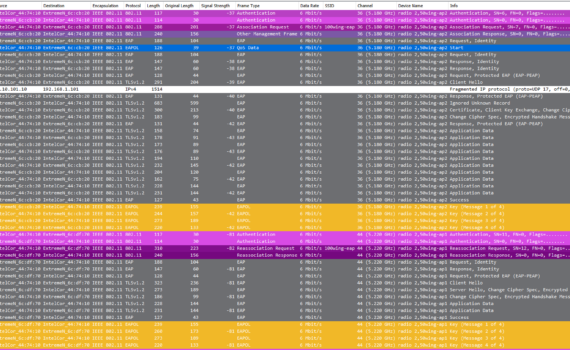
To jump straight into the “How To” without the “blabla”-intro, scroll down to section “How To – Setting Up Wireshark to do Multi-Channel / Multi-Source Captures” Intro While the Packet Capture functionality within the Ekahau Analyzer App is my go-to tool for Multi-Channel Captures (https://www.ekahau.com/rsc/ekahau-analyzer-packet-capture-overview/) there are 2 main scenarios […]
Blog
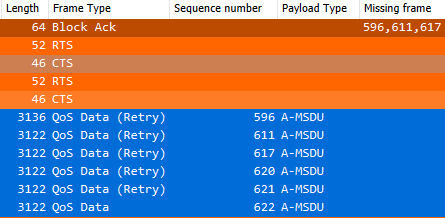
Whether you’re studying for exams like CWNA or CWAP, or you’re just in the deep ends of your Wi-Fi configuration, you probably come across the topic of frame aggregation – A-MSDU and A-MPDU in particular.Even though the study guides for above exams and some blogs (mrn-cciew, dot11ap) explain the concepts […]
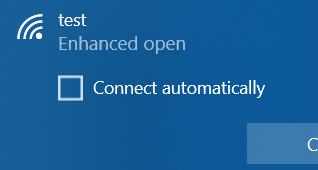
Back in spring 2019, Windows 10 introduced support for WPA3-Personal with its version 1903 update.Almost exactly one year later, they now also added the support for WPA3-Enterprise in the 2004 version update:Support for Wi-Fi Protected Access 3 (WPA3) on Intel® Wireless Adapters While I was playing around with some netsh-commands […]
Normally when you troubleshoot roaming issues, you have to go on-site with a multi-channel packet-capture device (for every channel you want to capture on, you need an individual NIC, since you can only capture on one concurrent channel per NIC), get a hold on the mobile device with said issues, […]
Introduction It all started with people telling me that when they were gathered in a meeting room, everybody loses their connection to the Wi-Fi. This happened sporadically and everyone got disconnected at the same time. Obviously the AP and the Wi-Fi were thought of being the source of this problem, […]
Introduction This post is about the effect of rate limiting on Wi-Fi and is inspired by the presentation Troy Martin (@troymart) gave at WLPC 2018 Prague (Link) and his recent appearance in the Clear To Send (@cleartosend) podcast episode 157 (Link) Especially his comparison between “configuring rate limiting” vs. “disabling […]
Introduction As a WiFi admin, you are probably familiar with WiFi Data Rates and the concept of DRS (Dynamic Rate Switching/Shifting/Selection). Numbers like 6Mbit/s, 54MBit/s, 144MBit/s, 300MBit/s and 400MBit/s all look pretty familiar – but what are they based on? The numbers are not random at all – the data […]
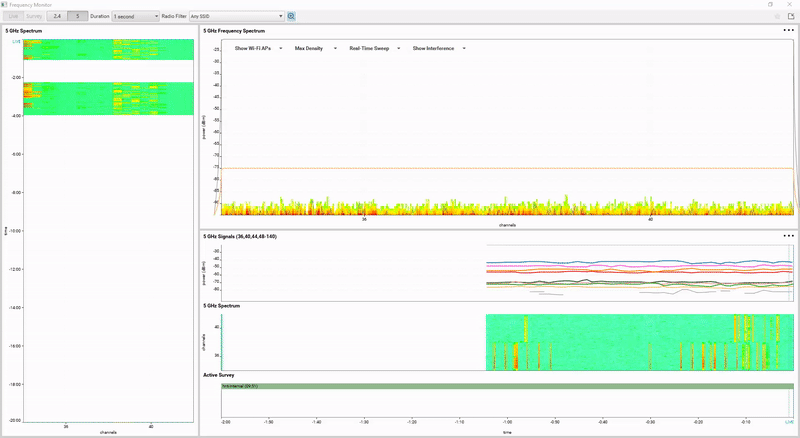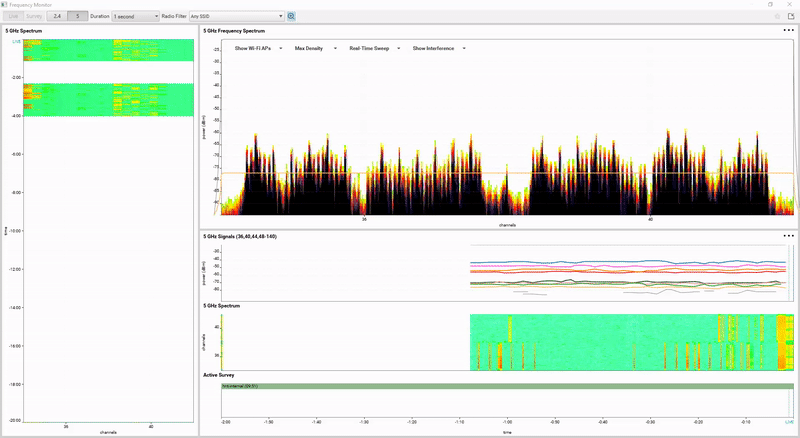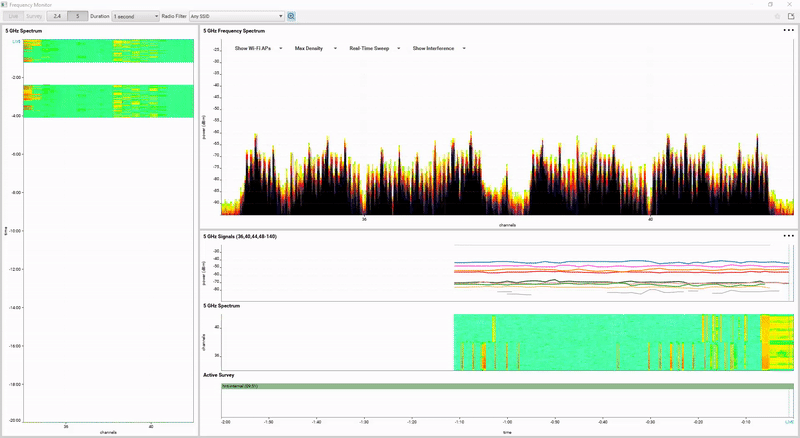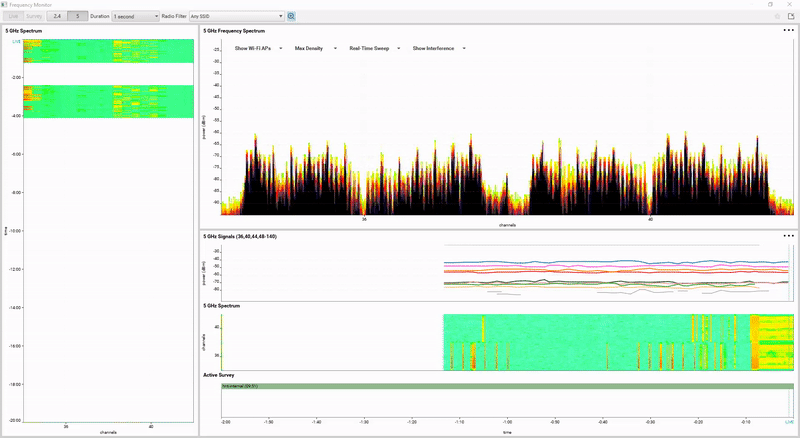
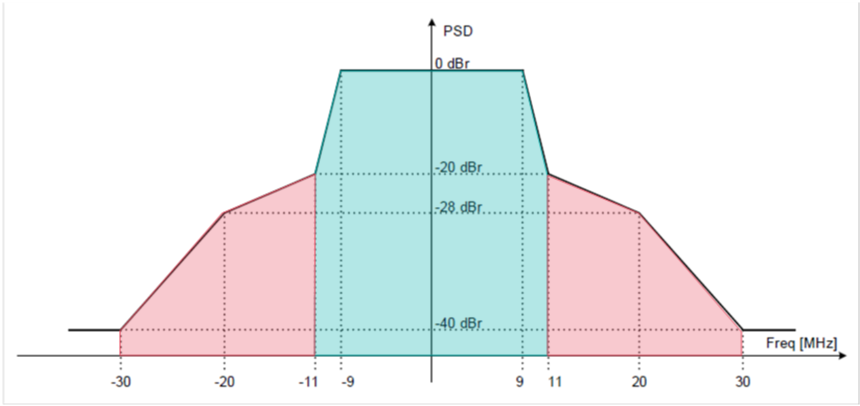
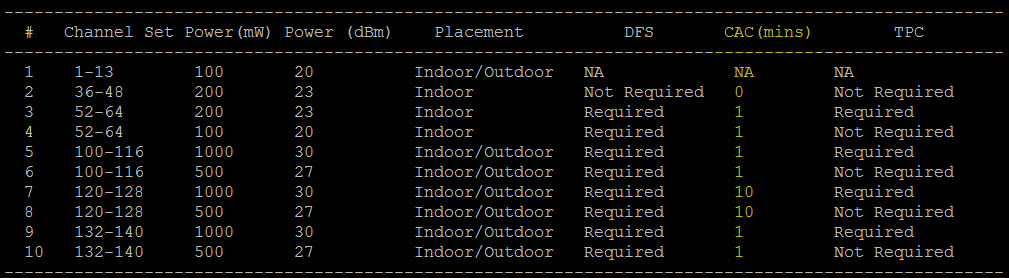
Introduction Whether we are designing, troubleshooting or just reading about Wireless LANs, we come across the catchword ‘ACI’ (Adjacent Channel Interference). While most people are familiar with the concept of Overlapping ACI in the 2.4GHz frequency band (‘Don’t use Channel 1 and Channel 2 in neighboring BSSes, because they overlap’ […]
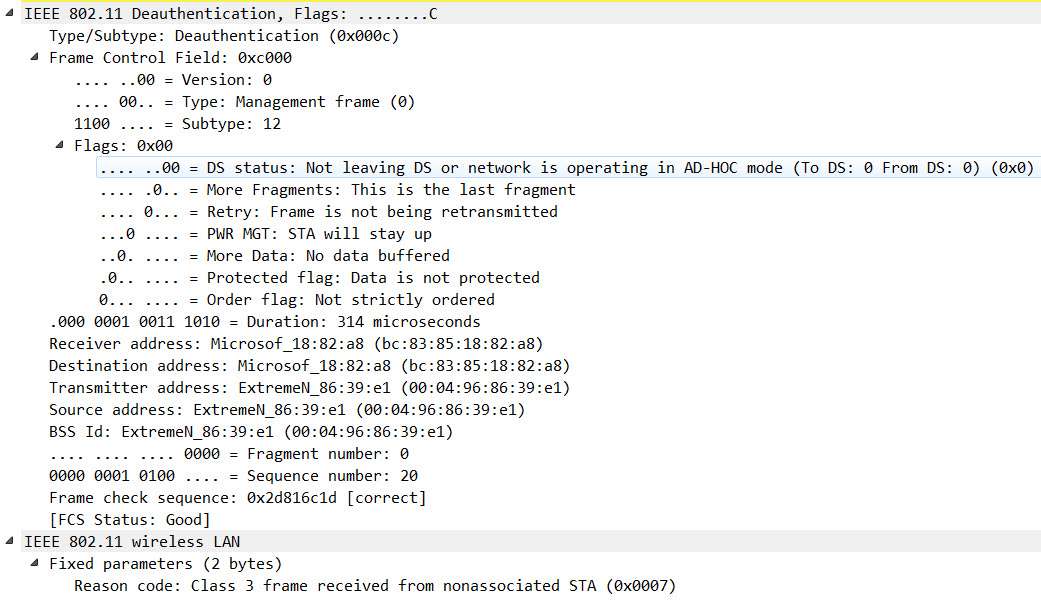
Introduction The goal of the 802.11w amendment, which was ratified in 2009 and consolidated in the IEEE Std 802.11-2012, was to introduce a way to secure management frames against attacks. The best known attacks this amendment should eliminate are the “deauthentication” and “disassociation” attacks, which can be used for multiple […]
Introduction Many times, there are small adjustments you have to implement in your live Wireless LAN environments. I personally am often faced with changes like these: – Adding a new SSID – Removing an unused SSID – Renaming an existing SSID – Changing the security settings (for example PSK) of […]