Back in spring 2019, Windows 10 introduced support for WPA3-Personal with its version 1903 update.
Almost exactly one year later, they now also added the support for WPA3-Enterprise in the 2004 version update:
Support for Wi-Fi Protected Access 3 (WPA3) on Intel® Wireless Adapters
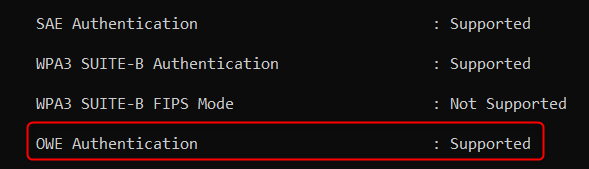
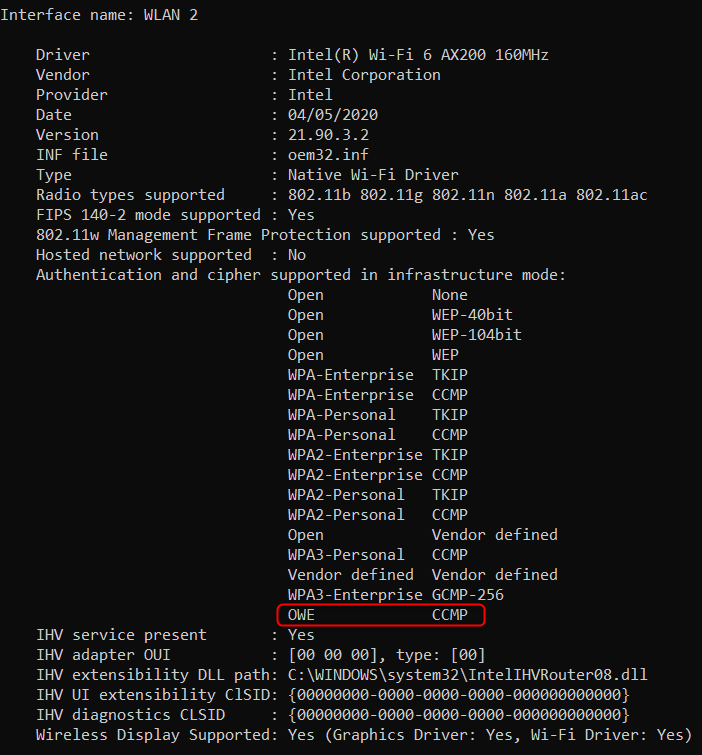
While I was playing around with some netsh-commands in Windows 10 version 2004, I stumbled across a new feature that was nowhere mentioned:
Not only did they add “WPA3 SUITE-B Authentication” (WPA3-Enterprise) to Windows 10 version 2004, they also added “OWE Authentication” (Enhanced Open).
Up until now, clients that were connected to an Open SSID (often found in restaurants, hotels, events, etc.) did not have any layer 2 encryption. They were reliant on upper-layer encryption such as HTTPS, SSH, SMTPS to protect their traffic from eavesdropper. But since lots of network traffic (such as DNS, HTTP, SMTP) is sent in cleartext, Open SSIDs are susceptible for those kind of attacks.
With Enhanced Open / OWE, Wi-Fi traffic gets encrypted at Layer 2 and is therefore protected against passive attacks. But please note that OWE is not a protection against active attacks such as MITM (Man in the Middle), since OWE was introduced only for encryption but not for authentication. Therefore, it is still strongly recommended to use a VPN software!
Connect OWE capable Clients to an Enhanced Open SSID
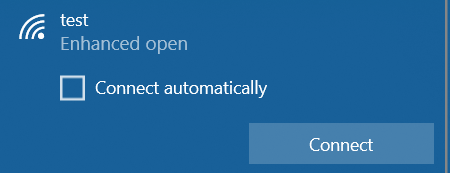
When you want to connect a client to an SSID that has OWE configured, it now says “Enhanced open” (but only if your client / Wireless NIC also supports OWE).
Note that it does not contain a lock and the text “Secured” next to it as with WPA/WPA2/WPA3-Protected SSIDs, since this feature does not include authentication and only adds encryption to Open SSIDs:
After successfully connecting to the Enhanced Open SSID, you can check the established connection via “netsh wlan show interfaces”:
Connect OWE incapable Clients to an Enhanced Open SSID
When you just enable “Enhanced Open” on your guest SSID, you would lock out every client that does not support it – which in mid-2020 is the vast majority of all clients. Therefore, it is strongly recommended to setup “Enhanced Open” in transition mode for years (if not decades) to come, so clients that do not support this feature can still connect to your guest network (see section “Additional Ressources” for more details).
Below is an example of a test client that does not support OWE Authentication and that was still able to connect to the guest network thanks to the SSID being configured in Transition Mode:
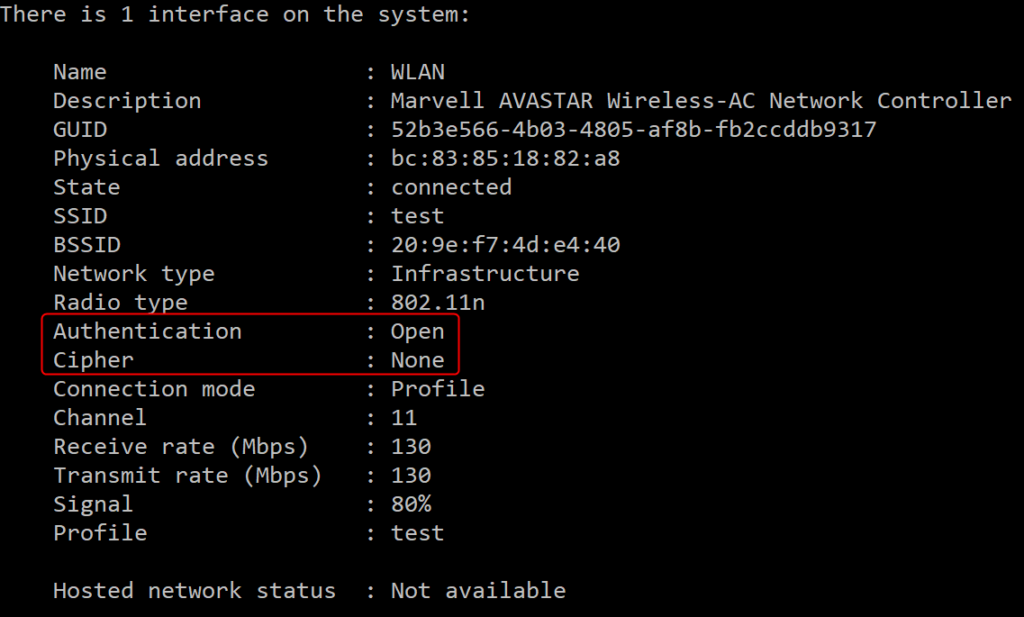
This client does not recognize the SSID as Enhanced Open, but just as a regular Open SSID:
After successfully connecting to the SSID, you can see that the client does not use any Cipher:
Additional Ressources
If you want to learn, how Enhanced Open works in detail, I can recommend the following ressources:
Benefits of WPA3, Enhanced Open, and Easy Connect: Deep Dive Presentation of Philipp Ebbecke and Perry Correll @WLPC Prague 2018
https://mrncciew.com/2019/11/21/enhanced-open-part-1/: Enhanced Open
https://mrncciew.com/2019/11/22/enhanced-open-part-2/: Enhanced Open – Transition Mode
https://wificoops.com/2019/08/05/wi-fi-security-enhancements-part-2-enhanced-open-owe/: Enhanced Open & configuration example on Cisco